Advertiser Disclosure
We independently review everything we recommend. When you buy through our links, we may earn a commission.
How to Use VPN: Complete Guide for Beginners and Experts

When Sarah first heard about VPNs from a colleague who worked remotely, she thought they were only for tech professionals or people doing shady online activities. Fast forward six months, and she wouldn’t dream of connecting to her coffee shop’s Wi-Fi without one. Like Sarah, millions of people discover daily that VPNs have become as essential as antivirus software for anyone serious about online privacy.
The reality is striking: over 1.75 billion people now use VPNs on a regular basis. That represents roughly one-third of all internet users worldwide, transforming what was once niche software into a mainstream necessity. Whether you’re protecting sensitive work documents, streaming your favorite shows while traveling, or simply browsing without advertisers tracking your every click, understanding how to use a VPN properly makes the difference between genuine protection and false security.
This comprehensive guide walks you through everything from selecting your first VPN service to mastering advanced features that most users never discover. We’ll use real-world examples and practical scenarios to demonstrate exactly how VPN technology works in everyday life.
Understanding What a VPN Actually Does
Picture your internet connection as a busy highway where every car represents a piece of your data traveling between your device and various websites. Without a VPN, anyone positioned along that highway can see exactly where you’re going, what you’re carrying, and where you came from. Your internet service provider, government agencies, hackers on public networks, and even your nosy neighbor with the right tools can monitor your digital travels.
A Virtual Private Network transforms that exposed highway into a secure tunnel. My most recommended VPN is NordVPN, your device creates an encrypted connection to one of their servers before your data continues to its final destination. This process accomplishes two critical functions: it hides your real location by substituting the server’s IP address for yours, and it encrypts all your data so that even if someone intercepts it, they see only meaningless scrambled information.
The practical implications extend far beyond theoretical privacy concerns. Consider Maria, a freelance graphic designer who frequently works from cafes around her city. Without VPN protection, anyone on the same Wi-Fi network could potentially intercept her client communications, steal her login credentials, or monitor which websites she visits. When she connects through NordVPN’s servers, her laptop creates a secure tunnel that protects her sensitive project files and personal information from other network users.
The encryption happens automatically and invisibly. Modern VPN services use AES-256 encryption, the same standard employed by banks and government agencies to protect classified information. This level of security ensures that even if malicious actors intercept your data, breaking the encryption would require computational resources beyond what most criminals possess.
Beyond security, VPNs provide location flexibility that proves invaluable for various legitimate purposes. Business travelers often discover that their company’s internal systems become inaccessible when they travel abroad, while entertainment enthusiasts find their streaming subscriptions suddenly restricted based on geographic location. VPNs solve these problems by allowing you to appear as if you’re browsing from different locations worldwide.
Choosing Your VPN Service: What Actually Matters
The VPN market presents dozens of options, but the differences between services significantly impact your experience and security. Understanding what distinguishes quality providers from questionable ones helps you make informed decisions rather than falling for flashy marketing claims.
Premium services like NordVPN invest heavily in infrastructure that directly affects your daily experience. They operate thousands of servers across multiple countries, ensuring you always have fast, reliable connections regardless of your location or time of day. When you connect to NordVPN’s network, sophisticated load-balancing systems automatically route your traffic through servers with optimal capacity, preventing the sluggish performance that plagues overcrowded networks.
The technical specifications matter more than most users realize. Look for providers that offer multiple VPN protocols, particularly WireGuard and OpenVPN. WireGuard represents the cutting edge of VPN technology, delivering excellent speed with minimal battery drain on mobile devices. OpenVPN remains the gold standard for security-focused users who prioritize protection over raw performance. Quality services allow you to switch between protocols based on your immediate needs.
Server diversity extends beyond simple quantity. NordVPN maintains servers in over 60 countries, but more importantly, they operate multiple server types optimized for specific purposes. Their standard servers handle everyday browsing and streaming, while specialized servers optimize for peer-to-peer file sharing, enhanced security through double encryption, or accessing services that aggressively block VPN traffic.
The no-logs policy represents perhaps the most critical feature to verify. Legitimate VPN providers undergo independent security audits to prove they don’t store records of user activities. NordVPN has commissioned multiple third-party audits of its infrastructure and policies, providing documented evidence that it cannot provide user data to authorities even if compelled by legal orders.
Customer support quality becomes crucial when technical issues arise. Premium services provide 24/7 support through multiple channels, with representatives who understand the technical complexities of VPN connections. This support proves invaluable when you encounter configuration problems, connection failures, or need guidance on optimizing settings for specific use cases.
Setting Up Your VPN: Step-by-Step Walkthrough
The process of getting your VPN operational has become remarkably straightforward, though the specific steps vary slightly depending on your device and chosen provider. We’ll walk through the complete process using NordVPN as our example, covering the details that can trip up new users.
Windows Installation and Configuration
Begin by visiting NordVPN’s official website and creating your account. Avoid downloading VPN software from third-party sites, as modified versions sometimes contain malware or backdoors that compromise the security you’re trying to achieve. After completing your subscription, you’ll receive download links and login credentials via email.
The Windows application downloads as a standard installer file. During installation, Windows may display security warnings asking for permission to install network components. These permissions are necessary for the VPN to function properly, as the software needs to modify your network settings to route traffic through encrypted tunnels.
Once installed, launch the NordVPN application and log in with your credentials. The interface presents a world map showing available server locations, along with a simple connect button for quick connections. For your first connection, try clicking the quick connect feature, which automatically selects the optimal server based on your location and current network conditions.
After connecting, verify that your VPN is working correctly by visiting whatismyipaddress.com or similar services. Your displayed IP address should show the location of the NordVPN server you’re connected to, not your actual location. If you see your real IP address, the connection failed, and you should contact customer support.
The Windows application includes several important settings worth configuring immediately. Enable the kill switch feature, which blocks all internet traffic if your VPN connection drops unexpectedly. This prevents data leaks during temporary connection failures. You can also configure the application to launch automatically when Windows starts and connect to your preferred server without manual intervention.
macOS Setup Process.
Mac users follow a similar process, though macOS presents slightly different permission requests during installation. Download the NordVPN application from either their website or the Mac App Store. The App Store version receives updates automatically, while the direct download version allows you to control update timing.
During initial setup, macOS requests permission to add VPN configurations to your system. This permission is essential for the software to establish encrypted connections. The system also asks for administrator credentials to install the necessary network extensions.
The macOS application integrates seamlessly with the menu bar, providing quick access to connection controls without opening the full application window. This integration allows you to connect, disconnect, or switch servers with just a few clicks, making VPN usage feel natural rather than cumbersome.
Mac users particularly benefit from NordVPN’s IKEv2 protocol, which handles network transitions smoothly. When your MacBook switches between Wi-Fi networks or wakes from sleep mode, IKEv2 automatically reestablishes the VPN connection without requiring manual intervention.
Mobile Device Configuration
Smartphone and tablet users represent the fastest-growing segment of VPN adoption, with 64% of smartphone users regularly employing VPN services. Mobile VPN setup follows the same basic principles as desktop installation, but mobile-specific features provide additional convenience and security.
Download the NordVPN application from your device’s official app store. Both iOS and Android versions offer identical core functionality, though the interfaces differ slightly to match platform conventions. During setup, the applications request permission to create VPN configurations on your device.
Mobile VPN applications excel at automatic protection features that desktop versions cannot match. NordVPN’s mobile apps include auto-connect functionality that activates the VPN whenever you join untrusted Wi-Fi networks. This feature proves invaluable for frequent travelers who connect to various public networks throughout their journeys.
The mobile applications also include battery optimization features specifically designed for smartphones and tablets. The WireGuard protocol, available in NordVPN’s mobile apps, provides excellent security while consuming minimal battery power compared to older protocols.
Split tunneling functionality allows mobile users to route specific applications through the VPN while allowing others to connect directly. This feature helps conserve cellular data when using data-intensive applications that don’t require VPN protection.
Router-Level Installation for Network-Wide Protection
Installing VPN software directly on your router protects every device on your network simultaneously, from smart TVs and gaming consoles to IoT devices that cannot run VPN applications individually. Though only 8% of current VPN users employ router-level protection, this approach offers significant advantages for households with multiple connected devices.
Router VPN installation requires more technical knowledge than device-specific applications. First, verify that your router supports VPN functionality or consider purchasing a VPN-compatible router if your current model lacks this capability. Many modern routers include built-in VPN support, while others require custom firmware like DD-WRT or OpenWrt.
NordVPN provides detailed configuration files and setup instructions for popular router models. The process typically involves downloading configuration files from your NordVPN account dashboard and uploading them to your router’s administration interface. Each server location requires a separate configuration file, so you’ll need to decide which locations you want available on your router.
Once configured, every device that connects to your network automatically benefits from VPN protection without individual app installations. This approach particularly benefits devices like smart TVs, gaming consoles, and streaming devices that cannot run traditional VPN applications.
Router-level VPN connections do present some limitations. Switching server locations requires accessing your router’s admin panel rather than simply clicking a button in an application. Additionally, all network traffic routes through the same VPN server, so you cannot customize protection on a per-device basis.
Mastering VPN Protocols and Settings
Understanding VPN protocols helps you optimize your connection for specific situations rather than accepting default settings that may not suit your particular needs. Modern VPN services like NordVPN offer multiple protocol options, each with distinct advantages and optimal use cases.
WireGuard represents the newest generation of VPN technology, built from the ground up with modern cryptographic principles and streamlined code. When you select WireGuard in NordVPN’s settings, you benefit from exceptional connection speeds and battery efficiency that older protocols cannot match. The protocol’s minimal codebase makes it easier to audit for security vulnerabilities while maintaining excellent performance across all device types.
OpenVPN remains the gold standard for users who prioritize security over raw speed. This protocol has undergone extensive security analysis over many years, building a reputation for reliability and strong encryption. NordVPN’s OpenVPN implementation uses AES-256 encryption with perfect forward secrecy, ensuring that even if encryption keys become compromised, previously transmitted data remains secure.
IKEv2 excels in mobile environments where network conditions change frequently. When your smartphone switches between Wi-Fi and cellular connections or moves between different cell towers, IKEv2 quickly reestablishes VPN connections without lengthy reconnection delays. This protocol particularly benefits users who maintain VPN connections during commutes or travel.
The kill switch feature deserves special attention because it prevents data leaks during connection failures. When enabled in NordVPN’s settings, the kill switch monitors your internet connection continuously. If the VPN connection drops for any reason, the kill switch immediately blocks all internet traffic until the VPN reconnects. This protection proves crucial when handling sensitive information or when operating in locations where internet surveillance presents genuine risks.
Split tunneling allows sophisticated users to customize which applications use VPN protection and which connect directly to the internet. NordVPN’s split tunneling implementation lets you specify individual applications or websites that should bypass the VPN connection. This feature helps optimize performance for local services while maintaining protection for sensitive activities.
DNS configuration often receives insufficient attention despite its security implications. When you connect to NordVPN’s servers, the service automatically configures your device to use its secure DNS servers rather than your internet provider’s DNS. This configuration prevents DNS hijacking attacks and ensures that your browsing requests don’t leak information to third parties.
Advanced VPN Techniques for Power Users
Beyond basic connection and protection, VPNs offer sophisticated features that can significantly enhance your online experience and security posture. These advanced techniques require more setup effort but provide capabilities that basic VPN usage cannot achieve.
NordVPN’s Double VPN feature routes your internet traffic through two separate VPN servers in different countries, creating multiple layers of encryption and making it extremely difficult to trace your online activities. When you enable Double VPN, your data travels from your device to the first NordVPN server, then through an encrypted tunnel to a second server before reaching its final destination. This approach provides exceptional anonymity for users with heightened privacy requirements.
The performance impact of Double VPN connections is significant, typically reducing connection speeds by 50% or more compared to single-server connections. Reserve this feature for situations where maximum privacy outweighs performance considerations, such as when researching sensitive topics or communicating about confidential matters.
Obfuscated servers address the challenge of VPN detection and blocking that users face in restrictive environments. Some countries, corporations, and streaming services actively identify and block VPN traffic. NordVPN’s obfuscated servers disguise VPN traffic to appear like regular encrypted web traffic, making it much more difficult for detection systems to identify and block.
These specialized servers prove invaluable for users in countries with internet restrictions or for accessing services that aggressively block VPN connections. The obfuscation process adds some latency to connections, but the ability to maintain access often justifies the performance cost.
Dedicated IP addresses represent another advanced feature that some users find essential. Unlike standard VPN connections that share IP addresses among multiple users, dedicated IPs provide you with a unique address that only you use. NordVPN offers dedicated IP addresses in several countries, providing consistency that benefits specific use cases.
Online banking systems often flag shared VPN IP addresses as potentially fraudulent, leading to account locks or additional verification requirements. Dedicated IP addresses eliminate these issues by providing consistent login locations that banking systems recognize as legitimate. Similarly, users who manage social media accounts or online businesses benefit from the consistency that dedicated IPs provide.
The technical implementation of dedicated IPs requires additional configuration during setup. You’ll receive specific connection details for your dedicated IP server, which you must configure manually in your VPN application. The process varies by device but typically involves creating a custom connection profile rather than using the automatic server selection features.
Troubleshooting Common VPN Problems
Even premium VPN services occasionally experience technical difficulties, and understanding how to diagnose and resolve common problems helps maintain consistent protection and performance. Most VPN issues fall into predictable categories with established solutions.
Connection failures represent the most frequent problem users encounter. When your VPN refuses to connect, start by verifying your internet connection works without the VPN active. If your regular internet connection functions properly, try connecting to different NordVPN servers. Server maintenance, overcrowding, or network issues can affect specific servers while leaving others operational.
Firewall and antivirus software sometimes interfere with VPN connections by blocking the network changes necessary for tunnel establishment. Temporarily disable these security programs to test whether they’re preventing VPN connectivity. If disabling security software resolves the connection problem, configure exceptions for your VPN application rather than leaving security programs permanently disabled.
DNS leaks present a more subtle but potentially serious problem. Even when your VPN connection appears to function normally, your device might still send DNS requests directly to your internet provider’s servers rather than through the VPN tunnel. These leaked requests can reveal your browsing activity despite VPN protection.
Test for DNS leaks using online tools like dnsleaktest.com or ipleak.net. When connected to NordVPN, these tools should show only NordVPN’s DNS servers in their results. If you see your internet provider’s DNS servers or other unexpected entries, your DNS requests are leaking outside the VPN tunnel.
Resolving DNS leaks often requires manual DNS configuration. In NordVPN’s settings, look for options to use custom DNS servers and configure your device to use only NordVPN’s DNS addresses. Some users prefer third-party DNS services like Cloudflare (1.1.1.1) or Quad9 (9.9.9.9) for additional privacy and performance benefits.
Speed problems frustrate users who experience significant performance degradation when using VPN connections. All VPNs introduce some speed reduction due to encryption overhead and additional network hops, but dramatic slowdowns often indicate specific issues with server selection or configuration.
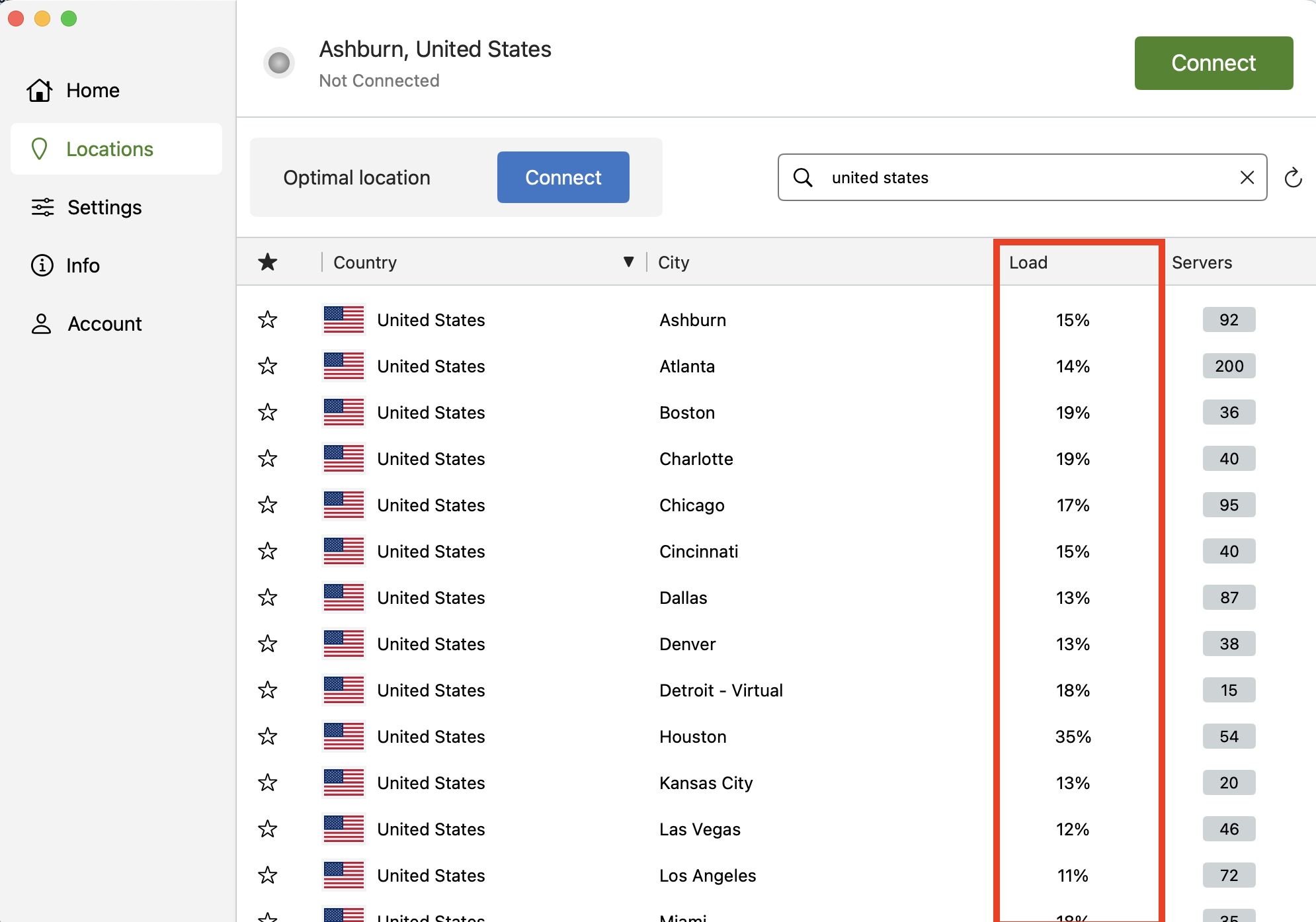
Try connecting to different NordVPN servers, particularly those geographically closer to your location. Server distance significantly affects latency, while server load impacts overall throughput. NordVPN’s applications typically display server load percentages, helping you identify less crowded options that may provide better performance.
Protocol selection dramatically affects speed performance. Switch between WireGuard, OpenVPN, and IKEv2 protocols to identify which provides optimal performance for your specific network conditions. WireGuard generally offers the best speed, while OpenVPN prioritizes security over performance.
Streaming service blocks present increasingly common challenges as entertainment platforms become more sophisticated at detecting VPN usage. Netflix, Hulu, BBC iPlayer, and other services actively identify and block IP addresses associated with VPN servers.
NordVPN maintains specialized streaming servers optimized for accessing geo-restricted content. These servers use IP addresses that streaming services haven’t identified as VPN-related, though the ongoing cat-and-mouse game between VPN providers and streaming services means that working servers change frequently.
When you encounter streaming blocks, contact NordVPN’s customer support for current server recommendations. Their support team maintains up-to-date information about which servers currently work with specific streaming services.
VPN Security Best Practices and Limitations
Maximizing VPN effectiveness requires understanding both the technology’s capabilities and its limitations. VPNs provide excellent protection for many online activities, but they cannot solve every security challenge you might face.
Keep your VPN applications updated to benefit from security patches and performance improvements. NordVPN regularly releases updates that address newly discovered vulnerabilities, improve connection stability, and add new features. Enable automatic updates when possible, or check for updates manually on a regular schedule.
Use strong, unique passwords for your VPN accounts and enable two-factor authentication when available. Your VPN account credentials provide access to all your encrypted internet traffic, making them valuable targets for attackers. NordVPN offers two-factor authentication through authenticator applications, adding an essential security layer to your account.
Avoid free VPN services that finance their operations through advertising, data collection, or selling user information to third parties. These services often provide inadequate security, maintain detailed logs of user activities, and may inject advertisements into your browsing sessions. The operational costs of running secure VPN infrastructure make truly free services financially unsustainable without compromising user privacy.
Understand that VPNs cannot protect against all online threats. They secure your internet connection but cannot prevent malware infections, phishing attacks, or social engineering scams. Maintain comprehensive security practices that include regular software updates, cautious email handling, and skeptical evaluation of suspicious websites or communications.
Legal considerations vary significantly by jurisdiction. While VPNs are legal in most countries, some nations restrict or ban their usage entirely. Research local laws before using VPN services when traveling internationally, particularly in countries known for internet restrictions or surveillance.
The trust relationship between you and your VPN provider represents a critical security consideration. Using a VPN requires trusting your provider with all your internet traffic, making provider selection crucial for maintaining privacy and security. Research providers thoroughly, focusing on their privacy policies, audit history, and jurisdiction of operation.
VPNs protect your data in transit, but cannot secure information stored on your devices or in cloud services. Encrypt sensitive files separately using disk encryption or file-level encryption tools. This layered approach ensures that your data remains protected even if device theft or cloud service breaches occur.
Business and Enterprise VPN Applications
Organizations employ VPN technology differently than individual consumers, focusing on secure remote access, regulatory compliance, and protecting sensitive business communications. Understanding business VPN applications helps organizations implement effective security strategies while enabling flexible work arrangements.
Remote access VPNs allow employees to securely connect to corporate networks from home offices, client sites, or while traveling. When configured properly, these connections provide access to internal resources while maintaining the same security controls that protect on-premises activities. NordVPN’s business solutions include centralized management features that allow IT administrators to monitor and control VPN usage across entire organizations.
Site-to-site VPNs create secure connections between multiple business locations, effectively extending corporate networks across geographic boundaries. A company with offices in New York and London can use site-to-site VPN connections to allow seamless access to shared resources as if both locations were on the same local network.
Bring Your Device policies rely heavily on VPN technology to secure personal devices accessing corporate resources. When employees use personal smartphones, tablets, or laptops for work purposes, VPN connections help isolate corporate data from personal activities while providing necessary security controls.
Compliance requirements in industries like healthcare, finance, and legal services often mandate VPN usage to protect sensitive client information. HIPAA, PCI-DSS, GDPR, and similar regulations require organizations to implement technical safeguards that protect personal and financial data during transmission. VPN encryption helps organizations meet these requirements while enabling necessary business communications.
Employee training represents a critical component of business VPN implementations. Organizations must educate staff about proper VPN usage, including when to activate connections, how to verify connection status, and what activities require VPN protection. Comprehensive training programs reduce security incidents while ensuring that VPN investments provide intended protection.
Audit and monitoring capabilities become essential for organizations that must demonstrate compliance with regulatory requirements. Business-grade VPN services provide detailed logging and reporting features that help organizations track VPN usage, identify potential security incidents, and generate compliance reports for regulatory audits.
Future Trends in VPN Technology
VPN technology continues evolving to address emerging threats, changing user expectations, and new regulatory requirements. Understanding these trends helps users and organizations prepare for future developments while making informed decisions about current VPN investments.
Quantum-resistant encryption represents one of the most significant upcoming changes in VPN technology. As quantum computing capabilities advance, current encryption methods may become vulnerable to quantum-based attacks. VPN providers are already researching and implementing post-quantum cryptographic algorithms that will remain secure even against quantum computers.
Zero-trust network architecture fundamentally changes how organizations approach network security. Rather than trusting devices and users based on their network location, zero-trust models verify every connection attempt regardless of VPN usage. This approach complements VPN technology while adding additional security layers that protect against insider threats and compromised credentials.
Artificial intelligence and machine learning technologies are being integrated into VPN services to automatically optimize performance, detect security threats, and improve user experience. NordVPN and other providers use AI algorithms to analyze network conditions and automatically select optimal servers for specific user requirements.
Privacy regulations continue expanding globally, creating new requirements for VPN providers and users. The European Union’s GDPR, California’s CCPA, and similar regulations worldwide are establishing new standards for data protection that affect how VPN services operate and how organizations implement VPN policies.
Integration with cloud services represents another significant trend as organizations migrate infrastructure and applications to cloud platforms. VPN providers are developing specialized solutions that integrate seamlessly with Amazon Web Services, Microsoft Azure, Google Cloud Platform, and other major cloud providers.
Mobile-first development reflects the reality that smartphones and tablets represent the primary internet access method for many users worldwide. VPN providers are redesigning their services with mobile users as the primary consideration, rather than treating mobile applications as secondary products.
Conclusion
VPN technology has evolved from a niche tool used by technology professionals into essential software for anyone serious about online privacy and security. The transformation reflects both the increasing sophistication of internet threats and the growing awareness among users about the importance of protecting their digital activities.
Understanding how to properly select, configure, and use VPN services empowers you to take control of your online privacy while accessing the full potential of internet connectivity. Whether you’re protecting sensitive business communications, securing personal browsing on public networks, or accessing geo-restricted content while traveling, VPNs provide powerful capabilities that enhance your digital experience.
The key to successful VPN implementation lies in matching service capabilities to your specific requirements rather than assuming all VPN providers offer equivalent protection and performance. Premium services like NordVPN invest heavily in infrastructure, security audits, and user experience improvements that directly benefit your daily internet usage.
As internet threats continue evolving and privacy concerns intensify worldwide, VPN adoption will likely continue expanding across all user demographics. Staying informed about VPN technology developments and best practices ensures you can adapt to changing requirements while maintaining optimal protection for your digital activities.
Remember that VPNs work most effectively as components of comprehensive security strategies rather than standalone solutions. Combining VPN protection with strong passwords, regular software updates, careful browsing habits, and healthy skepticism toward suspicious communications creates a robust defense against modern internet threats.
The investment in understanding and properly implementing VPN technology pays dividends in enhanced privacy, improved security, and expanded access to global internet resources. Take the time to configure your chosen VPN service properly, and you’ll benefit from protection that enhances rather than complicates your online activities.